Page 37 - EngineerIt March 2021
P. 37
INDUSTRY, TECHNOLOGY AND INNOVATION
Exploits on organisations worldwide grew tenfold after
Microsoft’s revelation of Four Zero-days
By Yaniv Balmas, Head of Cyber Research, Lotem Finkelsteen, the
head of Threat Intelligence, Adi Ikan, Head of Network Research and
Protection, Sagi Tzadik, Security Researcher
ollowing the revelation of four zero-day vulnerabilities currently
Faffecting Microsoft Exchange Server, Check Point Research (CPR)
discloses its latest observations on exploitation attempts against
organisations that it tracks worldwide.
• CPR has seen thousands of exploit attempts against
organisations worldwide
• CPR has observed that the number of attempted attacks has
increased tenfold from 700 on March 11 to over 7200 on March 15.
• The country most attacked has been The United States (17%
of all exploit attempts), followed by Germany (6%), the United
Kingdom (5%), The Netherlands (5%) and Russia (4%).
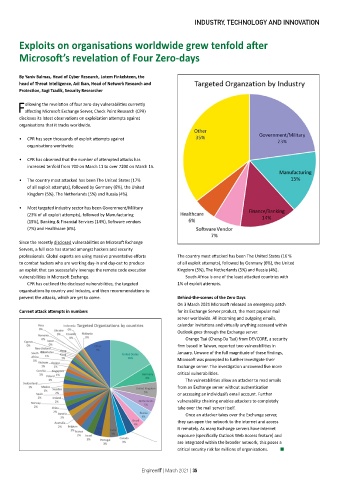
• Most targeted industry sector has been Government/Military
(23% of all exploit attempts), followed by Manufacturing
(15%), Banking & Financial Services (14%), Software vendors
(7%) and Healthcare (6%).
Since the recently disclosed vulnerabilities on Microsoft Exchange
Servers, a full race has started amongst hackers and security
professionals. Global experts are using massive preventative efforts The country most attacked has been The United States (16 %
to combat hackers who are working day-in and day-out to produce of all exploit attempts), followed by Germany (6%), the United
an exploit that can successfully leverage the remote code execution Kingdom (5%), The Netherlands (5%) and Russia (4%).
vulnerabilities in Microsoft Exchange. South Africa is one of the least attacked countries with
CPR has outlined the disclosed vulnerabilities, the targeted 1% of exploit attempts.
organisations by country and industry, and then recommendations to
prevent the attacks, which are yet to come. Behind-the-scenes of the Zero Days
On 3 March 2021 Microsoft released an emergency patch
Current attack attempts in numbers for its Exchange Server product, the most popular mail
server worldwide. All incoming and outgoing emails,
calendar invitations and virtually anything accessed within
Outlook goes through the Exchange server.
Orange Tsai (Cheng-Da Tsai) from DEVCORE, a security
firm based in Taiwan, reported two vulnerabilities in
January. Unware of the full magnitude of these findings,
Microsoft was prompted to further investigate their
Exchange server. The investigation uncovered five more
critical vulnerabilities.
The vulnerabilities allow an attacker to read emails
from an Exchange server without authentication
or accessing an individual’s email account. Further
vulnerability chaining enables attackers to completely
take over the mail server itself.
Once an attacker takes over the Exchange server,
they can open the network to the internet and access
it remotely. As many Exchange servers have internet
exposure (specifically Outlook Web Access feature) and
are integrated within the broader network, this poses a
critical security risk for millions of organisations. n
EngineerIT | March 2021 | 35