Page 10 - EngineerIt August 2021
P. 10
ICT SECURITY
Insider threat detection for security
and compliance
by John Mc Loughlin, J2 CEO*
Business leaders need to rethink server visibility, detection and protection, especially considering
the recent attacks on both businesses and the technology platforms that they run.
n today’s modern and distributed on both businesses and the technology platforms that they run.
enterprise, it’s more difficult than ever In virtually every successful attack there were obvious abnormal super-user account
Ito proactively combat internal and activities, anomalous file downloads and changes in packaged software processes. These
external threats due to a lack of server attacks all offered ‘indicators of intent’ that should have triggered elevated risk scores and
visibility in the context of user behaviour, immediate investigative action.
application updates and system Most leaders are still not aware that there are next-generation infrastructure
configuration changes. awareness capabilities to protect cloud, on-premises and virtual servers from data
This lack of visibility into data access, breaches, insider threats and outsider infiltration.
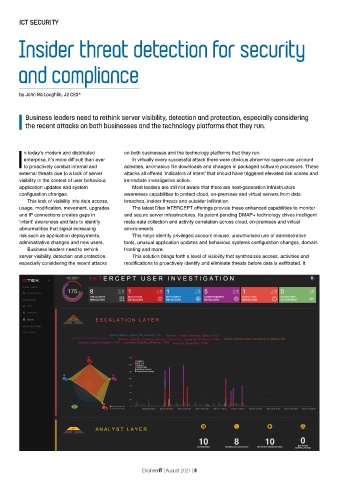
usage, modification, movement, upgrades The latest Dtex InTERCEPT offerings provide these enhanced capabilities to monitor
and IP connections creates gaps in and secure server infrastructures. Its patent-pending DMAP+ technology drives intelligent
‘intent’ awareness and fails to identify meta-data collection and activity correlation across cloud, on-premises and virtual
abnormalities that signal increasing environments.
risk such as application deployments, This helps identify privileged account misuse, unauthorised use of administrative
administrative changes and new users. tools, unusual application updates and behaviour, systems configuration changes, domain
Business leaders need to rethink fronting and more.
server visibility, detection and protection, This solution brings forth a level of visibility that synthesises access, activities and
especially considering the recent attacks modifications to proactively identify and eliminate threats before data is exfiltrated. It
EngineerIT | August 2021 | 8